Protect your PEN/USB Drive from Virus
 World is shrinking, and so are the data storage devices. One common device which every one use is USB devices like thumb drive, PEN drive, USB Hard disks etc...
World is shrinking, and so are the data storage devices. One common device which every one use is USB devices like thumb drive, PEN drive, USB Hard disks etc...
After floppy disks which were earlier prone to many viruses, now it is time for USB Devices. Below are some safety precautions that you may perform before transferring data from USB devices.
1) When you plug in the USB device in your system (Desktop / Laptop), you will most likely be prompted by a popup window as shown below.
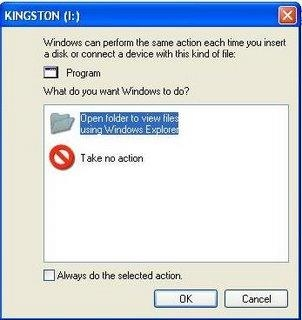
2) Dont select any of them, simply click cancel.
3) Goto Start -> Run and type cmd to open the Comman Prompt window
4) Now double click My Computer Icon (which is usually present in the desktop). It should show the list of drives available in this machine. Check the drive letter of the inserted USB Device. (As in above case it is (I:))
5) Go back to the command prompt and type the drive letter and hit Enter.
6) Now type the below command and hit Enter. This command displays all the hidden files and folders in the current working drive (I: Drive in our case)
I:\> dir/w/o/a/p
7) You will be able to see a list of files, after you run the above command. In the list, check if you see any one of the files mentioned below,
- Autorun.inf
- New Folder.exe
- Bha.vbs
- Iexplore.vbs
- Info.exe
- New_Folder.exe
- Ravmon.exe
- RVHost.exe
or any other unknown .exe files that you are unaware of and you have not copied to the device earlier.
8) If you find any one of the files listed above, you are right!!! you have got a virus in your USB device. Don't panic, it will be transferred to your system and start its duties only when you start copying the files to your computer's hard drive.
9) Now that you have confirmed that you have virus in your USB device, now type the following command and hit enter
I:\> attrib -h-r-s-a *.*
attrib command is for displaying and changing the attributes of the files.
10) Now Delete each of the files that you were not aware of and found to be on the above list by using the below command and hit enter
I:\> del <filename>
For eg. I:\> del Autorun.inf
11) That's it, you did it!!!!!!!! now your USB Device is free of virus.
Note: Some viruses are vulnerable to antivirus softwares. When unnoticed these viruses sits in system registry and doesnot allow the antivirus software to locate the source file. But it generates a virus child file in all the folders of the system. Antivirus software may detect the child file and delete it, but it keeps on generating. It cannot be stopped until source virus file is removed.
 In 2005 Intel revealed its 65-nm manufacturing process, then 45-nm in 2007. Today, in keeping with its "tick-tock" strategy, Intel is announcing a further shrinkage to its manufacturing process as it ends the development phase for 32-nm chip circuitry. That puts the chips on a production schedule for Q4 2009 -- interesting as Intel's rumored 32-nm Medfield chip wasn't expected until the first half of 2010. According to Intel, the new chips incorporate second-generation high-k + metal gate technology with transistors that switch 22% faster than its current 45-nm Penryn chips. Why should you care? Well, the smaller chips are cheaper to manufacture which should translate to consumer savings. They also require less power than Intel's notoriously power-friendly Atom-class chips. As an interesting side note, the Wall Street Journal is reporting that Intel has also disclosed a variant of its 45-nm process (the Lincroft-based Pine view we presume) "that is tailored to create chips for portable computing devices that require low power consumption." Uh, those wouldn't be targeting ARM by any chance would they Intel? Wink wink, nudge nudge.
In 2005 Intel revealed its 65-nm manufacturing process, then 45-nm in 2007. Today, in keeping with its "tick-tock" strategy, Intel is announcing a further shrinkage to its manufacturing process as it ends the development phase for 32-nm chip circuitry. That puts the chips on a production schedule for Q4 2009 -- interesting as Intel's rumored 32-nm Medfield chip wasn't expected until the first half of 2010. According to Intel, the new chips incorporate second-generation high-k + metal gate technology with transistors that switch 22% faster than its current 45-nm Penryn chips. Why should you care? Well, the smaller chips are cheaper to manufacture which should translate to consumer savings. They also require less power than Intel's notoriously power-friendly Atom-class chips. As an interesting side note, the Wall Street Journal is reporting that Intel has also disclosed a variant of its 45-nm process (the Lincroft-based Pine view we presume) "that is tailored to create chips for portable computing devices that require low power consumption." Uh, those wouldn't be targeting ARM by any chance would they Intel? Wink wink, nudge nudge.
 Cell phone radiation is spawning worries that it can do everything from
Cell phone radiation is spawning worries that it can do everything from 
 Today, Novatel introduced a portable 3G hotspot router, the sleek and minimalistic MiFi, which transforms 3G internet access into a Wi-Fi hotspot wherever it goes to multiple users.
Today, Novatel introduced a portable 3G hotspot router, the sleek and minimalistic MiFi, which transforms 3G internet access into a Wi-Fi hotspot wherever it goes to multiple users.
 The feature looks cool, and it’s exceedingly straightforward. When you’re in Gmail, your contact list will show a little green camera icon next to any buddy who has a Webcam, is online, and has installed the Gmail Voice and Video Chat plug-in (which works with IE 7, some versions of IE 6, Firefox, Safari, and, of course, Chrome). Click the icon, and you get a chat window with video in the bottom right-hand corner of the Gmail interface. (You can also blow it up to full-screen mode.)
The feature looks cool, and it’s exceedingly straightforward. When you’re in Gmail, your contact list will show a little green camera icon next to any buddy who has a Webcam, is online, and has installed the Gmail Voice and Video Chat plug-in (which works with IE 7, some versions of IE 6, Firefox, Safari, and, of course, Chrome). Click the icon, and you get a chat window with video in the bottom right-hand corner of the Gmail interface. (You can also blow it up to full-screen mode.)
 World is shrinking, and so are the data storage devices. One common device which every one use is USB devices like thumb drive, PEN drive, USB Hard disks etc...
World is shrinking, and so are the data storage devices. One common device which every one use is USB devices like thumb drive, PEN drive, USB Hard disks etc...










0 comments: