Installing Oracle Identity Management 11g R1 (11.1.1.1)
Introduction: Oracle Identity Management enables enterprises to manage the end-to-end lifecycle of user identities across all enterprise resources—both within and beyond the firewall. With Oracle Identity Management, you can deploy applications faster, apply the most granular protection to enterprise resources, automatically eliminate latent access privileges, and much more.
Oracle Identity Management 11g Release 1 (11.1.1) includes the following components:
- Oracle Internet Directory
- Oracle Directory Integration Platform
- Oracle Virtual Directory
- Oracle Directory Services Manager
- Oracle Identity Federation
In this post we will see the installation of Oracle Identity Management 11g R1 (11.1.1.1). As mentioned before the approach for installing Oracle 11g FMW components is different then those of 10g components, I will mention the approach for installing Oracle Identity Management 11g.
Brief Installation Steps:
Following are the brief steps for installing Oracle Identity Management 11g
1) Install database 11g (11.1.0.6 / 11.1.0.7) including configuring TNS and listener
2) Create repository using Oracle RCU (Repository Creation Utility)
3) Install WLS (weblogic Server) and create a middleware home
4) Install Oracle Identity Management 11g inside middleware home
The installation will install and configure the complete Identity Management and provide the access URLs.
Download Locations:
You can download all the required software from following location
Oracle Database 11g (11.1.0.6/11.1.0.7) – http://www.oracle.com/technology/software/products/database/index.html
Oracle IDM 11g – http://www.oracle.com/technology/software/products/middleware/htdocs/111110_fmw.html (Download the product Identity Management)
Oracle RCU – http://www.oracle.com/technology/software/products/middleware/htdocs/111110_fmw.html
Oracle WLS 10.3.1 – http://www.oracle.com/technology/software/products/ias/htdocs/wls_main.html
Step 1) Install database 11g including configuring TNS and listener
For this you can create a 11g database. Also create a listener on any available port and configure TNS for the database.
Step 2) Create repository using Oracle RCU (Repository Creation Utility)
Using RCU, you can create repository for IDM. You dont have to install RCU for using it. RCU comes as a zip file along with the identity management software download. Once you unzip you run <RCU_UNZIP>/bin/rcu binary
This will invoke a GUI. On the first page you can select “Create Repository” and click on next.
On the next page RCU will ask for database details in which you want to create the repository. The page will look as shown below
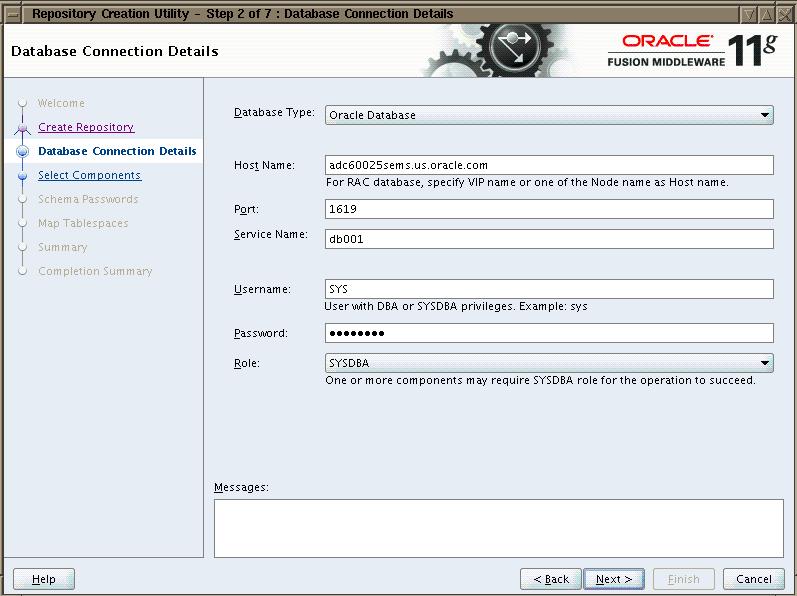
Once you connect to database, on the next page you need to select the repository that you want to create. Here you can select “Identity Management” as shown below. Also you can use any prefix for these schema. All these schema created will have the prefix string prefixed to it. In this case it will prepend DEV before each schema name. Note that it wont prefix anything before ODS schema. This schema is used for OID and SSO configuration.
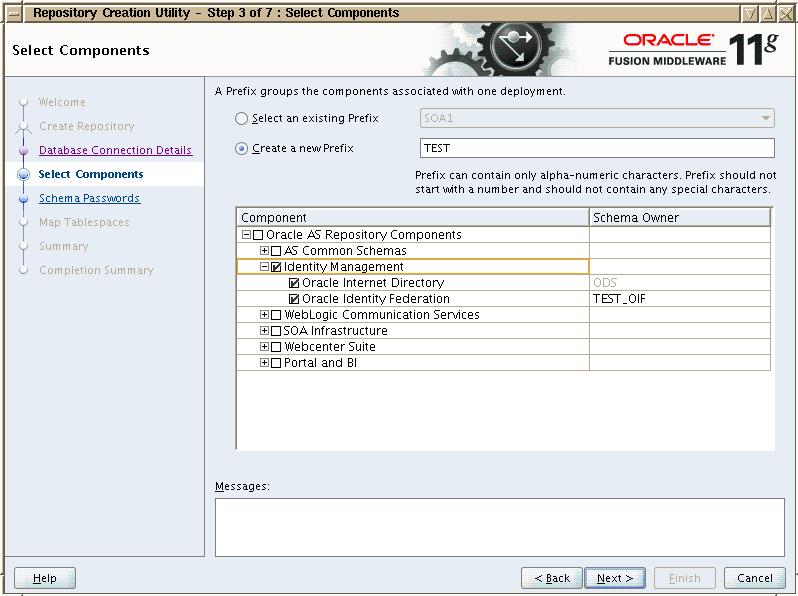
Once you click on next, it will show the summary and will create tablespace if they dont exists. After tablespace creation, click on create and it will create the required repository schemas.
Step 3) Install WLS (weblogic Server) and create a middleware home
Next step is to install WLS server. Carry out the basic installation of WLS. You need to provide a new location for middleware home when asked for as shown below.
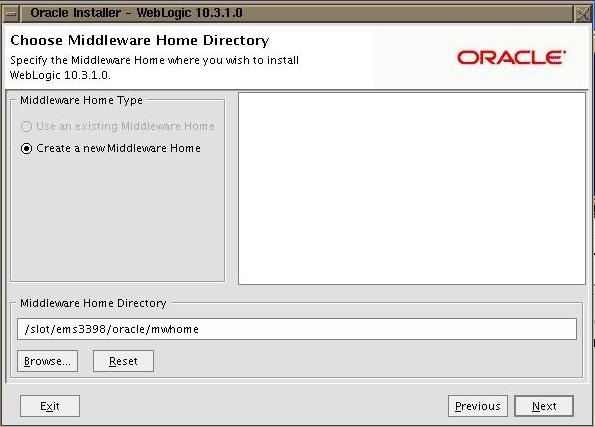
Next it will ask for the location of weblogic. Here you can accept the default value as it will be created inside middleware home.
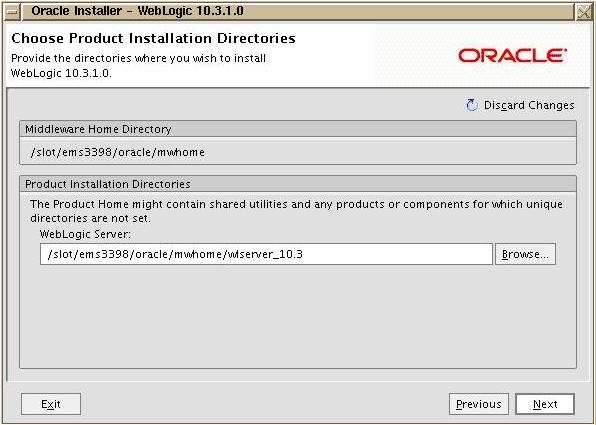
Select all other values as default and install WLS.
Step 4) Installing IDM 11g.
IDM installation involves many steps and screens. Please follow the below screen shots for installing IDM
When you start the IDM installer, you will see a welcome screen. Click on next.
Next you will see “Install option” screen. In this screen select “Install and Configure”. Click on next.
The installer will perform the pre-requisite checks. Click on next.
In the next screen “Select Domain”, click on “Create new domain” as shown below
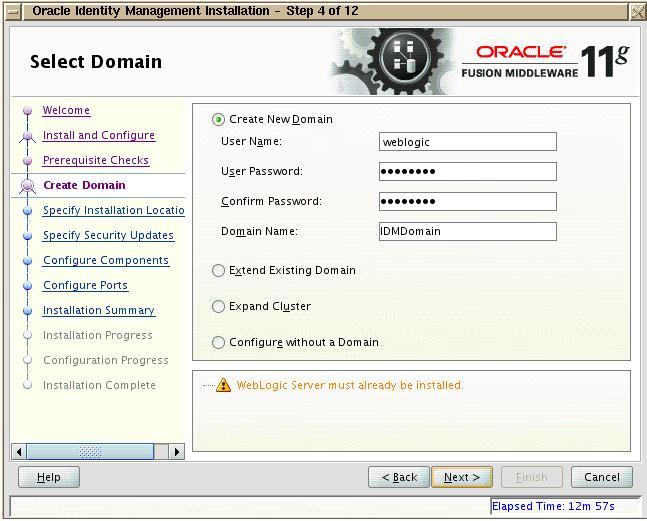
On the next screen, specify the install location inside middleware home.Click Next.
Select default values for next screen – Security Updates. Click Next.
On configure components screen, keep the default values. Click Next
On configure port screen, you can choose Automatic port assignment. Click Next.
On “Specify Oracle Virtual Directory Information” page, provide the inputs as shown in the screen below
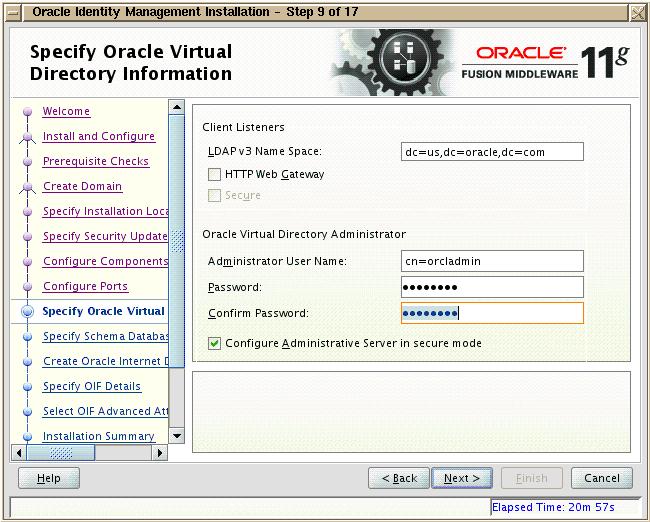
Here you need to specify the password for orcladmin. Remember the password you are setting here as you will need that at many places later. Click on Next.
On “Specify Schema Database” page, you can specify the ODS schema details that we created using repository creation utility (Step 2)). Also you need to provide ODS schema password you set while running RCU in step 2) as shown below

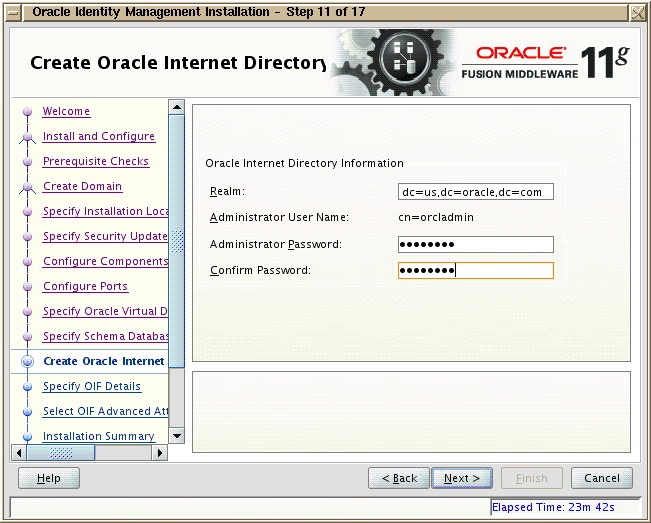
On “Create Oracle Internet Directory” screen, specify the Realm and orcladmin password. Note here that this orcladmin user is different then we say couple of screens back. This orcladmin user is for OID, where as the previous orcladmin user was for OVD.
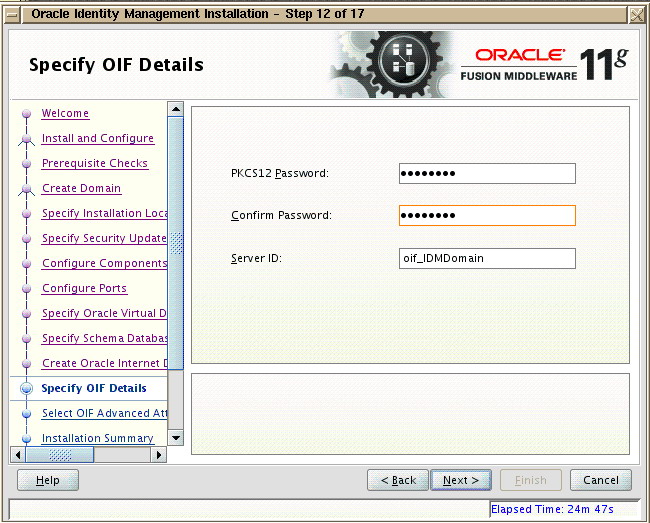
Next, On “Specify OIF Details” page, specify the PKCS12 password and the domain name for OIF as shown below
On rest of the screen, you can specify the default value and submit the installation. The installation will complete in approximately 45 mins. Once the installation and all configuration assistants completes successfully, you can login to weblogic console.
The default port for weblogic console is 7001. So the console URL becomes
http://<hostname>:7001/console
user name : Weblogic
password : As specified while installing WLS in step 3)

Once you login, you will see the managed servers created for OID and OIF.
Hope this helps !!






























0 comments: